In this article we will reveal the real scheme of deception when selling goods on one of the popular KUFAR ad platforms.BY, which almost caught one of the residents of the city of Svetlogorsk.
Let the analysis of the current situation serve as a lesson to others who may be targeted by an attacker.
We do not think that it is much different from other fraudulent schemes used in Belarus, Russia and other, mainly post-Soviet countries. Today, few people can imagine that Kufar, Onliner and other similar, popular online trading platforms can serve as the main source of collecting initial information for a fraudster who will flawlessly play the role of your buyer in the future. The rest of the production of the upcoming performance is only for him or his director.
So, a high chair is for sale. The ad shows the price, phone number, name of the seller.
All the newly submitted ads, even without VIP status and other paid ways to raise them, are in the center of attention of the largest possible circle of the Internet audience, which does not take long to wait in the feedback of a potential buyer.
The target is an ordinary housewife, apparently a young mother.

The key moment!
The dialogue is "tied" not through the Kufara chat and not through a direct call from a mobile operator, but through the Viber messenger (possibly through other WhatsApp, Telegram, etc.).
Not all the screenshots of these correspondences were saved, nevertheless, we will try to restore the chronology and form of the fraudulent scheme.
The buyer has the number of the Ukrainian operator +380 & hellip; (Sofia).
The dialogue begins in this style - the buyer has found what he has been looking for for so long, and here it is, this happy moment.

According to her, she is ready to pay immediately so that this product does not get to anyone else. She is not so much interested in the details of the product itself.
Believe me, it's so inspiring and gives some confidence to whoever is on the other side of your gadget.

«The buyer» is 100% sure about the presence of a European Post office in Svetlogorsk!

She is slightly annoyed by questions and some doubts on the part of the seller.
And at the same time, through the same Viber, a second potential client responds, whose dialogue style is very similar.
The second, allegedly the buyer, has the number of the Belarusian operator +375 …(Oleg).
Oddly enough, the SIM card number of the Belarusian subscriber did not exist (when trying to contact him through a mobile operator, the message "The subscriber with this number does not exist!" was issued), but communication was available via Viber.
The correspondence goes on in parallel.
There is absolutely no wariness yet, neither to the first buyer, nor to the second.

«There is no special difference to the buyer, through which the order will be placed - either by Euromail or Belpost. The link that he resets to fill in the transaction data looks the same. The main domain of which is belpost.bj
Pay attention to the link and its domain, which was provided by the "buyer" - belpost.bj
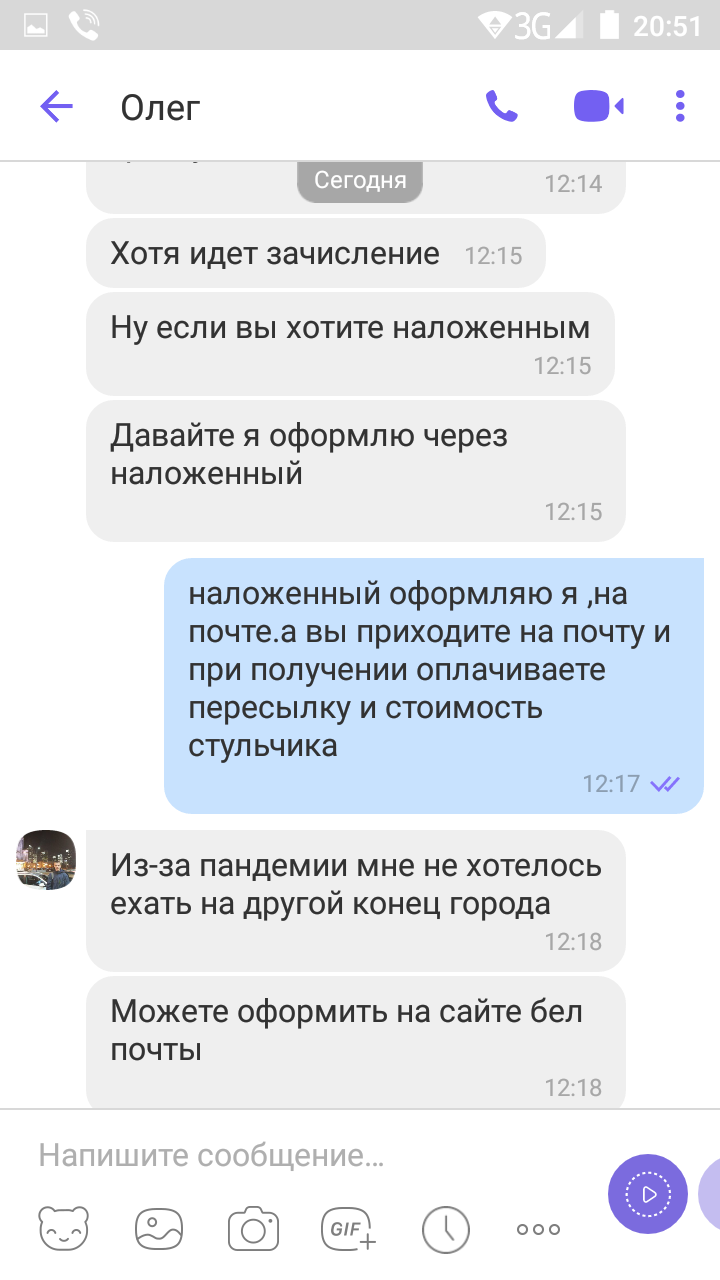
The seller resists, referring to a more convenient option for him - payment via cash on delivery, which is carried out directly at the post office itself.

«The buyer» insists on making the payment through the Belpost service (belpost.bj), and the other options just annoy him.
For complete conviction, he resets the screen of the delivery conditions by courier for the transaction through Kufar.

And here there is a certain confidence that these are really the terms of delivery regulated by Kufar.
When the buyer feels that you are ready to interact and have received some kind of trust from the correspondence, he offers you to fill out a form from the courier's website. In this case, it is either Euromail or Belpost.
We switch to the second buyer, who has already entered the seller's trust and convinced him to pay through the Belpost service - "belpost.bj"
Unfortunately, it was not possible to save the screen of the map data entry form, but the essence is this - the interface (appearance and external design of the site page) is identical to the Belpochta site (blue colors, similar navigation). Everything seems to be credible in the fact that Kufar and Belpost have worked hard in the development of some kind of online logistics service (payment-part-time). And why not!
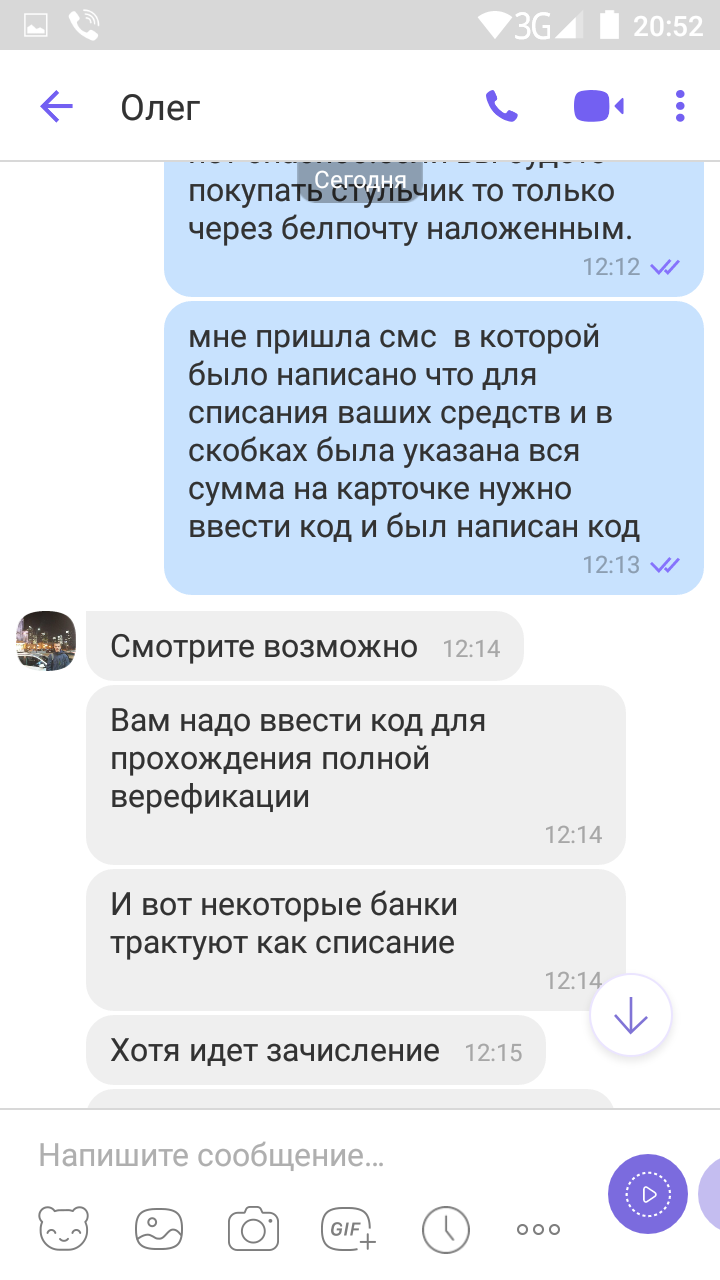
All card data (by our seller) were successfully entered into the submitted form - the bank card number, its expiration date and the security code (on its back). And it would seem that everything. BUT! The online bank's security system was triggered to confirm the operation, namely, an SMS notification came about the COMPLETE DEBITING OF ALL AVAILABLE FUNDS FROM the CARD.

And at that moment there was a kind of shake-up from the hypnosis hanging over the seller - he realized what would happen when the SMS operation was confirmed.
After that, a control call from the seller to the hotline to the bank follows, where it was confirmed that an attempt was made to write off funds in full.
The most interesting thing is that the dialogue with the fraudster, who had one step left to achieve his goal, continues.
The seller calls the buyer a fraudster, which he even resents.

Without losing hope, the fraudster continues to play the role of a bona fide buyer.
I am even ready to provide a passport, if only the seller would confirm the banking operation. It is clear that the passport hardly corresponds to the one who pretends to be the buyer.

But even this did not convince our seller. And that one, that other «buyer» were eventually sent......
How convincingly and professionally staged everything is!
According to available information, there are really affected residents not only of our city, but of other regions of Belarus, who lost impressive sums of money according to a similar scheme.
We think the competent authorities have already been informed about these atrocities. But the question is - will it be of any use ! But nevertheless...
What follows from all of the above !
- What kind of information is needed by a fraudster on your bank card ?
The number, its validity period and a three-digit secret code. - How can he use it ?
It would seem that having information about where the money is being debited, the bank could "calculate" the beneficiary of the payment and there it is up to law enforcement agencies. However, it is necessary to understand that today, having the data of any card and the settlement point online with the help of bank acquiring, money can not necessarily be debited to the settlement account of an identified user (which is more typical for online stores). Registration of bank-acquiring, which involves the possibility of calculating online through it from anywhere in the world, is provided not only to online stores, but also to online exchangers, exchanges where you can replenish your electronic and cryptocurrency wallets with fiat money. If there are diplomatic ties with Interpol, it is possible through the establishment of legal entities on which these exchanges are registered to identify the owners of these wallets and crypto accounts being replenished (through blockchain records). That is, it is necessary to conduct investigative actions with the competent authorities at the international level. And in today 's realities and the competence of state investigative bodies , this is practically impossible ! - Who in this case is an accomplice for "pulling" bank card data?
The developer of this software script - http://belpost.bj /...
The form for filling in the data on the bank card was opened when clicking on the link provided by the fraudster - https://belpost.bj / services/ Pochtovyyeotpravleniya0/ Peresylkadokumentov/ Posylki/ wrtaskqkiq
Trying to figure it out!
by and bj You catch the difference !
.bj is the national top-level domain for Benin. It was put into operation in 1996. The initiator of the introduction of the domain was Offices des Postes et Telecommunications. But this does not tell us anything, since today any user can buy any second-level domain, if it is not occupied by someone else.
Let's try « to break through » the registrar of this second-level domain.
To determine who owns the domain, through the Whois service, the procedure is quite complicated. Personal data is protected at the registrar level or hidden according to registry rules. It is doubtful to trust open data, since domain administrators can provide false information when registering a name. However, it can be seen that:

By Name Server (regery.com ) we determine where the site is physically located (although over the past time, the hosting could have changed repeatedly) – IP 138.201.79.102
Access to the Internet of this hosting was carried out through the provider hetzner.com , which is registered in Germany.

And now, as they say - try to find it!
Here is such a "weave" to unravel and search for the true developer (owner) of this link must be carried out.
To summarize !
Payments on the Internet using bank acquiring in Belarus are safe and convenient.
Just need to remember!
- Access to bank-acquiring (online payment points using a bank card) is currently provided only by payment aggregators WEBPAY, bePaid, Assist, EasyPay, ArtPay. That is, only through the websites of these companies it is possible to make online payments for products/services on the Internet.
- In no case do not enter your card data into the forms of incomprehensible pages (such as - belpost.bj !).
- If there are any doubts, verify the legitimacy of the Internet resource through which you want to make a purchase, for the right to carry out settlement and trading operations through the site BELGIE (Republican unitary enterprise for supervision of telecommunications) .
On the part of banks that are issuers and service card data, there should be responsibility for the security of payments made on the Internet by their customers. We think, at the program level, all these issues can be solved on their part.
Just don't dump the responsibility on the people themselves! For risks, the bank receives a monthly fee from its customers for servicing their cards.
The National Bank of the Republic of Belarus – AU!
Fraudulent scheme through Kufar – how almost divorced svetlogorets! - Something like that!































